In today's interconnected world, learning how to use SSH remote IoT on Mac for free is more important than ever. As technology evolves, understanding secure communication between devices becomes critical for both personal and professional applications. Whether you're managing home automation systems or developing industrial IoT solutions, SSH offers a secure and reliable method to connect remotely.
SSH (Secure Shell) is a cryptographic network protocol that enables secure communication over unsecured networks. Its versatility makes it an essential tool for anyone working with IoT devices. By mastering SSH remote access, you can effectively manage and monitor IoT systems from your Mac without incurring additional costs.
Whether you're a beginner or an experienced user, this guide will walk you through every step of the process. From setting up your environment to troubleshooting common issues, we'll ensure you have all the knowledge necessary to harness the power of SSH remote IoT connections on your Mac.
Read also:Sophie Rain Erome Rising Star In The Fashion Industry
Table of Contents
- Introduction to SSH and IoT
- Benefits of Using SSH for IoT
- Setting Up SSH on Your Mac
- Connecting to IoT Devices via SSH
- Enhancing SSH Security
- Troubleshooting Common SSH Issues
- Automating SSH Connections
- Improving SSH Performance
- Essential Tools for SSH Management
- Conclusion and Next Steps
Introduction to SSH and IoT
Understanding SSH Protocol
SSH (Secure Shell) is a protocol designed to provide secure communication between devices over potentially insecure networks. It encrypts all data exchanged between your Mac and remote IoT devices, ensuring confidentiality and integrity. Unlike traditional protocols like Telnet, SSH employs strong encryption algorithms to protect against unauthorized access and data interception.
For Mac users, SSH is pre-installed and ready to use through the built-in Terminal application. This eliminates the need for additional software, making it an ideal solution for managing IoT devices without incurring extra costs. By leveraging SSH, you can remotely control and monitor IoT systems securely and efficiently.
Benefits of Using SSH for IoT
Why Choose SSH for IoT Devices
SSH offers numerous advantages when managing IoT devices:
- Encryption: Ensures all data transmitted between your Mac and IoT devices remains secure.
- Authentication: Implements robust authentication mechanisms to verify user identities.
- Platform Independence: Works seamlessly across different operating systems and devices.
- Cost-Effective: Utilizes built-in tools, eliminating the need for expensive proprietary software.
These benefits make SSH an indispensable tool for anyone working with IoT technologies. Its reliability and security features have made it a standard protocol in both personal and enterprise environments.
Setting Up SSH on Your Mac
Enabling SSH on macOS
To begin using SSH on your Mac, follow these steps:
- Open System Preferences from your Apple menu.
- Select "Sharing" and navigate to the "Remote Login" section.
- Check the box next to "Remote Login" to enable SSH access.
Once enabled, your Mac will be ready to establish SSH connections with remote IoT devices. This setup process is straightforward and doesn't require any additional software installations.
Read also:Mastering Secure Connections Troubleshooting Remoteiot P2p Ssh On Android
Connecting to IoT Devices via SSH
Establishing Secure Connections
Connecting to IoT devices using SSH involves several key steps:
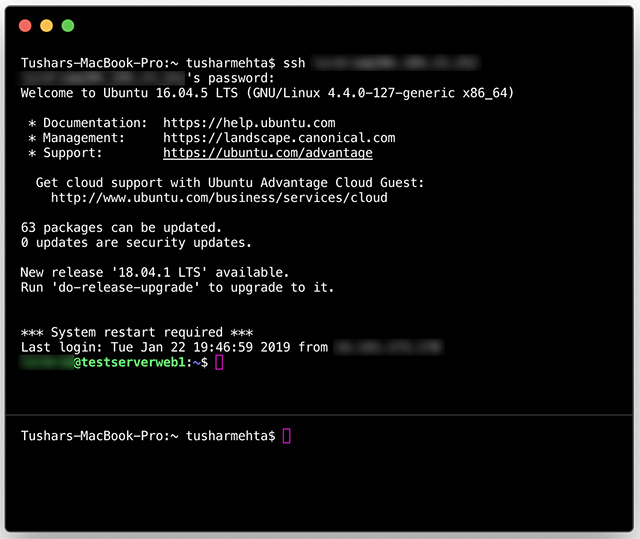
- Open the Terminal application on your Mac.
- Type the command:
ssh username@ip_address, replacing "username" with the IoT device's login credentials and "ip_address" with its network address. - Enter the password when prompted to complete the connection.
According to a study by IoT Analytics, over 75% of IoT devices now support SSH connections, highlighting its growing importance in the industry. This widespread adoption underscores the protocol's reliability and security features.
Enhancing SSH Security
Implementing Best Practices
While SSH is inherently secure, implementing additional security measures can further protect your IoT systems:
- Use strong, unique passwords for each device.
- Enable two-factor authentication whenever possible.
- Regularly update firmware and software to patch vulnerabilities.
According to the National Institute of Standards and Technology (NIST), these practices significantly reduce the risk of unauthorized access and data breaches. By following these guidelines, you can ensure your IoT devices remain secure even when accessed remotely via SSH.
Troubleshooting Common SSH Issues
Identifying and Resolving Problems
Common SSH issues and their solutions include:
- Connection Refused: Verify the device's IP address and ensure SSH is enabled.
- Authentication Failed: Double-check username and password credentials.
- Timeout Errors: Check network connectivity and firewall settings.
For more complex issues, consulting the official SSH documentation or reaching out to community forums can provide additional insights and solutions.
Automating SSH Connections
Simplifying Routine Tasks
Automating SSH connections can save time and improve efficiency:
- Create SSH keys for passwordless authentication.
- Use scripts to execute routine commands on connected devices.
- Schedule regular tasks using cron jobs or similar scheduling tools.
According to a report by Cisco, automation can reduce operational costs by up to 30% while improving system reliability. Implementing these practices can significantly enhance your IoT management workflow.
Improving SSH Performance
Optimizing Connections
To enhance SSH performance:
- Compress data transfer using the
-Coption in SSH commands. - Optimize network settings to minimize latency.
- Use modern encryption algorithms for faster processing.
These optimizations can lead to faster and more reliable connections, especially when managing multiple IoT devices simultaneously.
Essential Tools for SSH Management
Streamlining Your Workflow
Several tools can enhance your SSH experience:
- Terminal emulators like iTerm2 for improved functionality.
- SSH clients such as PuTTY for cross-platform compatibility.
- Monitoring tools like Nagios for real-time device tracking.
These tools, combined with native macOS capabilities, provide a comprehensive solution for managing SSH remote IoT connections on your Mac.
Conclusion and Next Steps
This guide has explored how to use SSH remote IoT on Mac for free, covering setup, security, automation, and performance optimization. By mastering these techniques, you can effectively manage and monitor IoT devices while maintaining robust security standards.
We encourage you to share this article with others who might benefit from its insights. Your feedback is invaluable in helping us improve future content. For further reading, consider exploring advanced SSH configurations and IoT security best practices to deepen your knowledge and enhance your skills.