RemoteIoT platform SSH key has become an essential tool for securing IoT devices in today's interconnected world. With the increasing reliance on remote access, having a robust security mechanism is more critical than ever. This guide will walk you through everything you need to know about using SSH keys with RemoteIoT platforms, ensuring your devices remain safe from unauthorized access.
As the Internet of Things (IoT) continues to expand, the need for secure communication between devices grows exponentially. RemoteIoT platforms provide a powerful solution for managing IoT networks, but their security depends heavily on proper implementation. SSH keys play a pivotal role in safeguarding these platforms, acting as a digital lock that only authorized users can open.
In this article, we will explore how to leverage SSH keys effectively within RemoteIoT platforms. From understanding the basics of SSH keys to advanced implementation techniques, you'll gain the knowledge necessary to protect your IoT infrastructure. Let's dive into the world of secure remote access and discover how SSH keys can enhance your RemoteIoT platform security.
Read also:Aziz Eloui Bey The Mastermind Behind Iconic Films
Below is the detailed table of contents to help you navigate through the article:
Table of Contents
- Introduction to RemoteIoT Platform SSH Key
- Understanding the Basics of SSH Keys
- Overview of RemoteIoT Platform
- How to Create SSH Keys for RemoteIoT
- Implementing SSH Keys in RemoteIoT
- Enhancing Security with SSH Keys
- Common Issues and Troubleshooting
- Best Practices for Using SSH Keys
- Alternative Solutions to SSH Keys
- Future Trends in RemoteIoT Security
Introduction to RemoteIoT Platform SSH Key
What is RemoteIoT Platform?
The RemoteIoT platform is a cutting-edge solution designed to manage and monitor IoT devices remotely. It provides users with the ability to control, configure, and gather data from IoT devices without physical access. This platform is particularly useful for businesses and organizations that rely on large-scale IoT deployments.
Why Use SSH Keys?
SSH (Secure Shell) keys serve as a secure authentication method for accessing remote servers and devices. Unlike traditional password-based authentication, SSH keys offer a higher level of security by eliminating the risk of brute-force attacks. By integrating SSH keys with RemoteIoT platforms, users can ensure that only authorized personnel gain access to their IoT networks.
Understanding the Basics of SSH Keys
SSH keys are cryptographic keys used to authenticate users in secure communication. They consist of two parts: a private key, which remains confidential and stored securely on the user's device, and a public key, which is shared with the server or device being accessed.
How Do SSH Keys Work?
- The user generates a pair of SSH keys using a key generation tool.
- The public key is uploaded to the server or device they wish to access.
- When the user attempts to connect, the server verifies their identity using the private key.
- If the keys match, the user is granted access without needing to enter a password.
Overview of RemoteIoT Platform
The RemoteIoT platform offers a suite of tools for managing IoT devices, including remote monitoring, data collection, and device configuration. It supports various communication protocols and integrates seamlessly with existing systems, making it a versatile choice for IoT management.
Key Features of RemoteIoT Platform
- Device Management: Easily add, remove, and configure IoT devices from a centralized dashboard.
- Data Analytics: Gain insights into device performance and usage patterns through advanced analytics.
- Security Protocols: Implement robust security measures, including SSH key authentication, to protect your IoT network.
How to Create SSH Keys for RemoteIoT
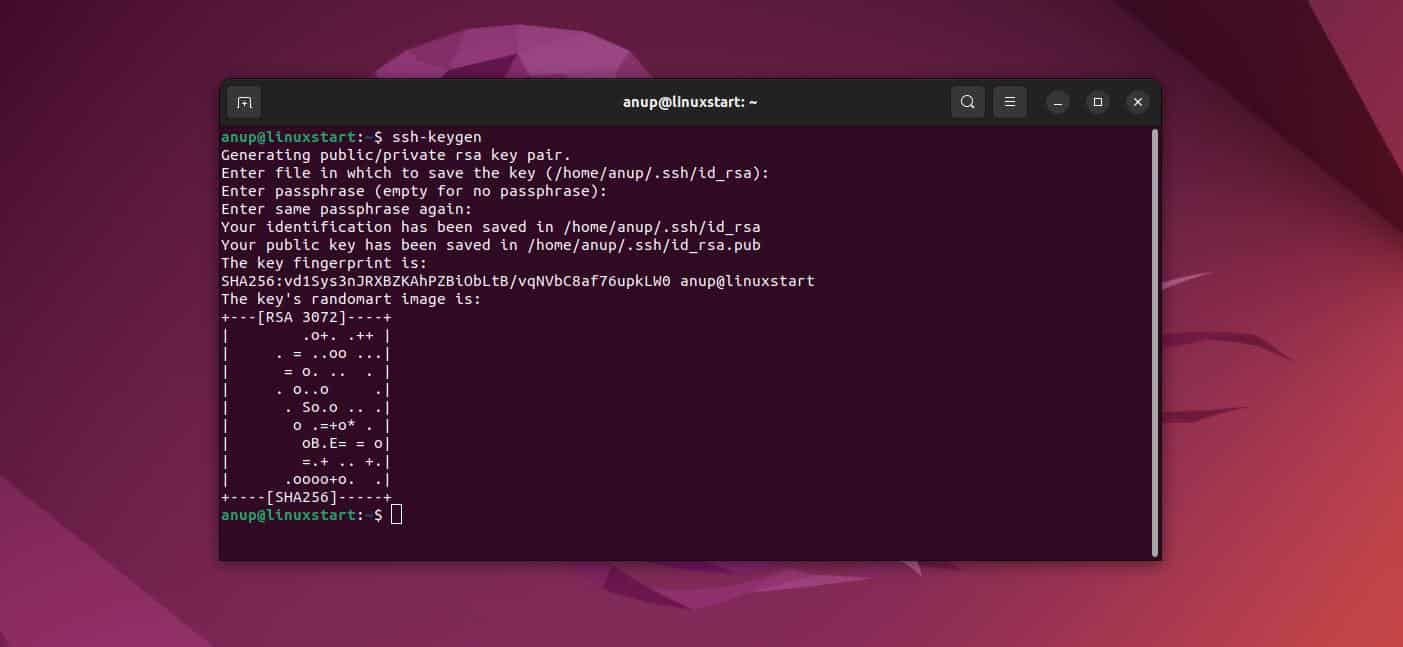
Creating SSH keys for your RemoteIoT platform involves a straightforward process. Follow these steps to generate and configure your SSH keys:
Read also:Unveiling The Phenomenon The Original Rise Of The Yes King
Step-by-Step Guide
- Open your terminal or command prompt.
- Run the command
ssh-keygen -t rsa -b 4096to generate a new RSA key pair. - Specify a file location to save the keys and set a passphrase for added security.
- Copy the public key to your RemoteIoT platform using the
ssh-copy-idcommand. - Test the connection to ensure the keys are working correctly.
Implementing SSH Keys in RemoteIoT
Once you have created your SSH keys, the next step is to integrate them into your RemoteIoT platform. This involves configuring the platform to recognize and use the keys for authentication.
Configuration Steps
- Access the RemoteIoT platform settings and locate the SSH key configuration section.
- Paste your public key into the designated field.
- Save the changes and restart the platform to apply the new settings.
- Verify that the SSH key authentication is functioning by attempting a connection.
Enhancing Security with SSH Keys
While SSH keys provide a strong foundation for secure access, additional measures can further enhance your RemoteIoT platform's security:
Additional Security Tips
- Regularly update your RemoteIoT platform to the latest version to patch any vulnerabilities.
- Implement two-factor authentication (2FA) for an extra layer of protection.
- Limit access to critical systems to only those who require it.
- Monitor access logs for any suspicious activity and take immediate action if necessary.
Common Issues and Troubleshooting
Despite their reliability, SSH keys can sometimes cause issues. Below are some common problems and solutions:
Problem: Connection Refused
Solution: Ensure that the SSH service is running on the RemoteIoT platform and that the firewall allows incoming connections on the appropriate port.
Problem: Key Not Recognized
Solution: Double-check that the public key has been correctly uploaded to the platform and that the private key matches the public key.
Best Practices for Using SSH Keys
Adopting best practices for SSH key management can significantly improve the security of your RemoteIoT platform:
Best Practices
- Use strong, unique passphrases for your private keys.
- Store private keys securely and avoid sharing them with others.
- Regularly rotate SSH keys to minimize the risk of exposure.
- Disable password-based authentication to force the use of SSH keys.
Alternative Solutions to SSH Keys
While SSH keys are a popular choice for secure access, other authentication methods are available:
Alternatives
- Public Key Infrastructure (PKI): Utilizes digital certificates for authentication.
- Token-Based Authentication: Employs tokens generated by hardware devices or mobile apps.
- Biometric Authentication: Relies on unique biological traits, such as fingerprints or facial recognition.
Future Trends in RemoteIoT Security
As technology continues to evolve, so too will the methods for securing RemoteIoT platforms. Emerging trends in IoT security include:
Trends
- Quantum-Resistant Cryptography: Developing encryption methods resistant to quantum computing attacks.
- AI-Powered Threat Detection: Leveraging artificial intelligence to identify and mitigate security threats in real-time.
- Zero-Trust Architecture: Implementing a security model that assumes all users and devices are untrusted until proven otherwise.
Conclusion
In conclusion, mastering RemoteIoT platform SSH key management is crucial for ensuring the security of your IoT infrastructure. By understanding the basics of SSH keys, implementing them correctly, and following best practices, you can protect your devices from unauthorized access.
We encourage you to share your thoughts and experiences with SSH keys in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT security and related topics. Together, we can build a safer, more connected world.
Data Source: National Institute of Standards and Technology (NIST), Cisco IoT Security